Trinity Int'l College
Model questions from NEB (SET-A)
------------------------------------------------
Model Question School Leaving Certificate Examination 2078 Grade: Grade XII Subject: Computer Science (Th) Subject code: 428 Full Marks: 50 (9 marks Obj + 41 Marks Sub) Time: 2 Hours
Group A: Multiple Choice questions (9 x 1=9) Time: 20 minutes
Tick the correct answer.
1. Which of the statements are used in DDL?
A) Create, alter and drop
B) Create, insert and select
C) Insert, update and delete
D) Delete, alter and drop
2. With SQL, how do you select all the records from a table named “Persons” where the value of the column “FirstName” ends with an “a”?
A) SELECT * FROM Persons WHERE FirstName=‟a‟
B) SELECT * FROM Persons WHERE FirstName LIKE „a%‟
C) SELECT * FROM Persons WHERE FirstName LIKE „%a‟
D) SELECT * FROM Persons WHERE FirstName=‟%a%‟
3. Which of the following statements is true about a star network topology?
A) Each device is connected to a switch or hub
B) Each device is connected to each other
C) Each device is connected in a trunk
D) Each device is connected to a terminal
4. Which of the following is the correct syntax to display "Stay Safe" in an alert box using JavaScript?
A) alert-box("Stay Safe");
B) confirm("Stay Safe");
C) msgbox("Stay safe");
D) alert("Stay Safe");
5. What is the use of <A> tag?
A) To insert an image
B) To create a link
C) To create a hyperlink
D) To create a list 139
6. What is the output of given C program?
void main()
{
char str1[] = "FIRST";
char str2[20];
strcpy(str2,str1);
printf("%s %s ",str1,str2);
printf("%d", (str1!=str2));
printf("%d", strcmp(str1,str2));
}
A) FIRST FIRST 0 0
B) FIRST FIRST 1 1
C) FIRST FIRST 1 0
D) FIRST FIRST 0 1
7. Where is a class derived in inheritance?
A) Superclass
B) Subclass
C) Subsetclass
D) Relativeclass
8. Which of these is the correct order of the SDLC?
A) Analysis, Design, Coding, Testing, Implementation
B) Analysis, Design, Testing, Implementation, Coding
C) Implementation, Coding, Analysis, Design, Testing
D) Design, Testing, Implementation, Coding, Analysis
9. Why is cloud computing popular nowadays?
A) Cost-sharing and easily accessible
B) As modern technology and costly
C) Accessible and freely available
D) Affordable to all
Group B: Short Answer Questions (5 x 5=25)
Explain 2NF and 3NF with examples.
OR
Demonstrate the basic DML statement with an example.
Write a function to add any two numbers in Javascript.
OR
Demonstrate the external CSS implemented in the web page.
12. Describe any five features of OOPs.
13. What are the different stages of software planning? Describe.
14. Define the concept of AI and IoT. (2+3)
Group C: Long Answer Questions (2 x 8=16)
15. How do you implement the Class C IP address in the local area network? Describe.
16. Write a program to enter ten integer numbers into an array, sort and display them in ascending order. OR
Write a program to read the marks of any 5 students in a subject and count how many students are pass and fail.
------------------------------------------------------------------------------------------------------------------------------------------
SET-B
Group A: Multiple Choice questions (9 x 1=9) Time: 20 minutes
Q1) To insert a record into a table, we use
Insert
Delete
Alter
All of the above
Q2) Which is a database software?
SQL
MYSQL
Oracle
All of the above
Q3) A topology where all the nodes are connected to each other.
Star
Bus
Tree
Mesh
Q4) In JavaScript, switch control structure supports
Integer values for case
Floating values for case
String values for case
All of the above
Q5) To use css codes in our HTML files, we enclose it between
<script> and </script>
<style> and </style>
<head> and </head>
None of the above
Q6) what would be the output?
#include <stdio.h>
int f(int x)
{
return x;
}
int main()
{
f(7);
printf("result=%d",f(8));
return 0;
}
0
9
2
8
Q7) The process of creating multiple classes from an existing class is called … inheritance.
Single
multiple
hierarchical
multilevel
Q8) ‘SDLC’ stands for
System Development Life Cycle
Standard Development Life cycle
Special Development Life Cycle
All of the above(a,b,c)
Q9) Which is the example of cloud?
a) Amazon Web Services (AWS)
b) Dropbox
c) Cisco WebEx
d) All of the above
Group B: Short answer questions (5x5=25)
Q10) Define the term ‘normalization’. Explain about 1N. [1+4]
Or
Explain about create, delete and alter commands used in SQL. [2+1+2]
Q11) What is a function in JS? Write a program to create a button, onclick of which displays an alert message. Use function. [2+3]
OR
Make a simple webpage using HTML and CSS. Include: [2+3]
->header for image
-> two columns of width 25% and 75%
Q12) Differentiate between procedure Oriented programming and Object-Oriented programming.[5]
Q13) What is a software development model? Explain about spiral model. [2+3]
Q14) Explain any two fields where we can use AI. [5]
Group C: Long Answer questions (2x8=16)
Q15) What is an IP address? What are its types? Under IPv4, how many classes are there? List them out. Differentiate between static and dynamic IP. [1+1+2+4]
Q16) Write a C program using structure to input employees’ id, name and salary. Then print that entered data in sorted format on the basis of salary (from highest to lowest). [8]
Or
Let, a datafile named “book.txt” contains information of books (name, price, edition). Write a program in C language to add some more data and then print all the records of books having price >900. [4+4]
SET-C
Group A: Multiple Choice questions (9 x 1=9) Time: 20 minutes
Which of the following is the basic structure of SQL to create table in data base…………………?
CREATE table (field1 data_type, field2 data_type,……)
CREATE table table_name (field1 data_type, field2 data_type,……)
CREATE table table_data (field1 data_type, field2 data_type,……)
All of the above
Which of the following is not example of DML (Data Manipulation Language)?
INSERT
UPDATE
DELETE
GRANT
Computer Network is
a. Collection of hardware components and computers
b. Interconnected by communication channels
c. Sharing of resources and information
d. All of the Above
…………………………… is not the phase of waterfall model.
Requirement analysis
Testing
Build prototype
Maintenance
Which of the following syntax is correct to embed JavaScript to HTML?
<script type=”text/javascript”></script>
<script language type=”text/javascript”></script>
<script type=”text/javascript language”></script>
All of the above
The prevention of data from unauthorized access is…………….
Data security
Data integrity
Data misuse
All of above
The delivery of computing services over the internet rather than having local servers or personal devices handle applications is called…………………
Cloud Computing
Analog Computing
Mobile Computing
All of the above
A variable which holds memory address of another variable is…………………….
Function
Pointer
Array
Structure
Binding the data with the code that manipulates it is ………………….
Polymorphism
Encapsulation
Inheritance
Abstraction
Group B: Short Answer Questions (5x5=25)
Explain Cloud Computing with its characteristics. [2+3]
What is DBMS? Write its advantages and disadvantages. [1+4]
OR
What is normalization? Write its advantages. [1+4]
WAP to display largest among three numbers using JavaScript.[5]
Explain OOP with its features. [5]
Explain SDLC with its phases. [5]
Group C: Long answer Questions (2x8=16)
Explain guided and unguided transmission media with its types. [4+4]
WAP to input name and address of 10 employees and sort them in ascending alphabetic order according to their name. [8]
OR
WAP to enter name, roll no and marks of 10 students and store them in a file. [8]
SET-D
Group A: Multiple Choice questions (9 x 1=9) Time: 20 minutes
Q1) The key that identifies each record uniquely, is called
Primary key
Unique key
Key record
Field name
Q2) Which forms simplifies and ensures that there are minimal data aggregates and repetitive groups:
a. 1NF
b. 2NF
C 3NF
D All of the mentioned
Q3) Which of the following is/are the main goals of a distributed database?
a. Interconnection of database
b. Incremental growth
c. Reduced communication overhead
d. All of the above
Q4) Which of the following is a ternary operator in JS?
A. -
b. ?:
c. +
d. :
Q5) PHP stands for …
Hypertext Processor
Hyper Markup Processor
c. Hyper Markup Preprocessor
c. Hypertext Preprocessor
Q6) What is the first octet value of class A IP?
0-126
128-191
224-239
192-223
Q7) The function
int fibo()
{
Statements;
}
Is called
Function declaration
Function definition
Function end
None of the above
Q8) What is an abstraction in object-oriented programming?
a) Hiding the implementation and showing only the features
b) Hiding the important data
c) Hiding the implementation
d) Showing the important data
Q9) Agile Software Development is based on which of the following type?
a. Iterative Development
b. Incremental Development
c. Both Incremental and Iterative Development
d. Linear Development
Group B: Short Answer Questions (5x5=25)
Q10) Differentiate between centralized and distributed database. [5]
Or
What is RDBMS? Explain relational model of a database. [2+3]
Q11) Write the difference between server side scripting and client side scripting. [5]
OR
Write steps to connect PHP code to your database. Let, database name is ‘test’. [5]
Q12) What are the different types of inheritance? Explain them. [5]
Q13) Describe in brief the process of prototype model. [5]
Q14) Define e-commerce and e-business. What are the advantages and disadvantages of e-commerce? [2+3]
Group C: Long answer Questions (2x8 =16)
Q15) Define communication system. Explain each component of communication system with necessary diagram. [1+2+5]
Or
Define OSI reference model. Explain each layer of OSI model. [1+7]
Q16) Differentiate between library and user defined function. Write a program to display largest among three numbers by using pointer. [4+4]
SET-E
Group A: Multiple Choice questions (9 x 1=9) Time: 20 minutes
Which of the following is a group of one or many attributes that uniquely identifies a row?
a. Key
b. Determinant
c. Tuple
d. Relation
In general, a file is basically a collection of all related
a. Rows & Columns
b. Fields
c. Database
d. Records
Give an example of half duplex mode of data communication.
TV
Radio
Walkie-Talkie
Internet
Which of the following can’t be done with client-side JavaScript?
a. Validating a form
b. Sending a form’s content by email
c. Storing the form’s contents to a database file on the server
d. None of the above
Which one of the following should not be used while sending password or other sensitive information?
a. GET
b. POST
c. REQUEST
d. NEXT
What will fopen will return if there is any error while opening a file?
Nothing
NULL
EOF
Depends upon compiler
Which feature of OOP indicates code reusability?
a) Abstraction
b) Polymorphism
c) Encapsulation
d) InheritanceWhich of the following is the first step in SDLC framework?
a. Feasibility Study
b. Requirement Gathering
c. Communication
d. System Analysis
Which segment of e-commerce model does eBay belong to?
a. B2B
b. B2C
c. C2B
d. C2C
Group B: Short Answer Questions (5 x 5=25)
What is RDBMS? Explain relational model of a database. [2+3]
Or
What is primary key? What are the features of good primary key? [1+4]
What is event handling in JavaScript? Explain with example. [2+3]
OR
What is variable? Write rules to variable in PHP. [1+4]
Define data abstraction and encapsulation. Mention their main advantages in OOP.[2+3]
Explain internet of thing (IOT) along with advantages and disadvantages.[5]
Describe in brief the process of agile model. [5]
Group C: Long Answer Questions (2x 8=16)
Define network topology. Describe star and ring topology with necessary diagram.[2+6]
Write a c program to input name, salary, and post of ‘n’ employee and sort them in alphabetical order according to their name. [8]
OR
Write a program to create a data file named ‘student.dat’ and store roll number, name and address of 10 students and display the record in proper format. [8]
SET-F
Group A: Multiple Choice Questions (9 x 1=9) Time: 20 minutes
Tick the correct answer.
1. ____ is a DDL command.
a) CREATE b) TRUNCATE c) ALTER d) all of the above
2. . Data dictionary is a repository that manages
a. Memory b. Metadata c. Spell Checker d. Data Validator
3. Mbps stands for?
Mega bits per second b) Mega bytes per second
Mega bands per second d) A and b
4. Which of the following is client side scripting language?
PHP b) HMTL c) CSS d) JavaScript
5. Which of the following is used to access html elements using javascript?
getElementById() b) getElementsByClassName()
Both a and b d) None of the above
6. For a function,
int series()
{
int a,I,s=0;
}
a,I and s are called
local variables
global variables
register variables
none of the above
7. Which is not feature of OOP in general definition?
a) Code reusability b) Modularity c) Duplicate/Redundant Data d) Efficient Code
8. What is the first step in the software development lifecycle?
system design b)Coding c) System testing d) Investigation and analysis
9. What is the name of the computer program that simulates the thought process of human being?
a) Human logic b) expert reason c) expert system d) personal information
Group B: Short Answer Questions (5 x 5=25)
What is primary key? Explain different data security methods. [2+3]
Or
Demonstrate the basic DDL statement with an example. [5]
11. What is JavaScript? Write a program in JavaScript to find the factorial of a given number. [1+4]
Or
Explain different types of PHP variables. [5]
12. Define object and class? What are the differences between a class and an object?[2+3]
13. What is feasibility study? Explain its types. [1+4]
14. What do you mean by robotics? Explain its characteristics. [1+4]
Group C: Long Answer Questions (2 x 8=16)
15. Define the term ‘communication protocol’. List any four protocols and explain any two. [2+2+4]
16. Write a program in C language to read name and marks of n number of students and store them in a file named ‘student.txt’. [8]
Or
Write a program to read the marks of any 5 students in a subject and count how many students are pass and fail. [8]
--------------------------------------------------------------------------------------------------------
Q How do you implement the Class C IP address in the local area network? Describe.
Classful Addressing
The 32 bit IP address is divided into five sub-classes. These are:
- Class A(0-127); 127 is excluded
- Class B(128-191)
- Class C(192-223)
- Class D(224-239)
- Class E(240-255)
Each of these classes has a valid range of IP addresses. Classes D and E are reserved for multicast and experimental purposes respectively. The order of bits in the first octet determine the classes of IP address.
IPv4 address is divided into two parts:
- Network ID
- Host ID
The class of IP address is used to determine the bits used for network ID and host ID and the number of total networks and hosts possible in that particular class. Each ISP or network administrator assigns IP address to each device that is connected to its network.
Class C:
- The network ID is 24 bits long.
- The host ID is 8 bits long.
- 2^21 = 2097152 network address
- 2^8 – 2 = 254 host address
- IP addresses belonging to class C ranges from 192.0.0.x – 223.255.255.x.
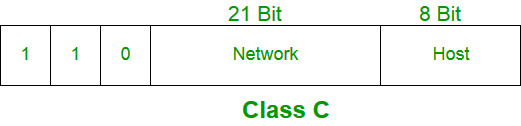
IP address belonging to class C are assigned to small-sized networks.
The higher order bits of the first octet of IP addresses of class C are always set to 110. The remaining 21 bits are used to determine network ID. The 8 bits of host ID is used to determine the host in any network. The default sub-net mask for class C is 255.255.255.x. Class C has a total of:
For example, you have a wide area network with 150 hosts on three networks (in different cities) that are connected by a TCP/IP router. Each of these three networks has 50 hosts. You are allocated the class C network 192.168.123.0. (For illustration, this address is actually from a range that isn't allocated on the Internet.) It means that you can use the addresses 192.168.123.1 to 192.168.123.254 for your 150 hosts.
You should now be able to give IP addresses to 254 hosts. It works fine if all 150 computers are on a single network. However, your 150 computers are on three separate physical networks. Instead of requesting more address blocks for each network, you divide your network into subnets that enable you to use one block of addresses on multiple physical networks.
In this case, you divide your network into four subnets by using a subnet mask that makes the network address larger and the possible range of host addresses smaller. In other words, you are 'borrowing' some of the bits used for the host address, and using them for the network portion of the address. The subnet mask 255.255.255.192 gives you four networks of 62 hosts each. It works because in binary notation, 255.255.255.192 is the same as 1111111.11111111.1111111.11000000. The first two digits of the last octet become network addresses, so you get the additional networks 00000000 (0), 01000000 (64), 10000000 (128) and 11000000 (192). (Some administrators will only use two of the subnetworks using 255.255.255.192 as a subnet mask. For more information on this topic, see RFC 1878.) In these four networks, the last six binary digits can be used for host addresses.
Using a subnet mask of 255.255.255.192, your 192.168.123.0 network then becomes the four networks 192.168.123.0, 192.168.123.64, 192.168.123.128 and 192.168.123.192. These four networks would have as valid host addresses:
192.168.123.1-62 192.168.123.65-126 192.168.123.129-190 192.168.123.193-254
Remember, again, that binary host addresses with all ones or all zeros are invalid, so you can't use addresses with the last octet of 0, 63, 64, 127, 128, 191, 192, or 255.
You can see how it works by looking at two host addresses, 192.168.123.71 and 192.168.123.133. If you used the default Class C subnet mask of 255.255.255.0, both addresses are on the 192.168.123.0 network. However, if you use the subnet mask of 255.255.255.192, they are on different networks; 192.168.123.71 is on the 192.168.123.64 network, 192.168.123.133 is on the 192.168.123.128 network.

No comments:
Post a Comment